Project Proposal And Plan (A2 Submission)
Written by Paul Tuohy
Project Title:
Classifying Revenge Porn: Evaluating Effective Techniques for the Classification of Non-consensual Content on Hosting Platforms.
Project Blog:https://paultuohy.com
Project Proposal
Abstract:
The ease to access and proliferate pornographic content online has placed a greater focus on an individual’s privacy and consent around content being shared online. In particular the proliferation of non-consensual ‘revenge porn’ content has become an area of concern. Manually monitoring content is impossible due to the vast amount of content available and the rate at which content can be reuploaded across multiple platforms. Therefore, developing advanced AI approaches to detect non-consensual porn are required to assist in preventing further proliferation. Unfortunately, current models are error-prone, suffer from skin-tone bias, or don’t utilise facial recognition techniques in classifying subjects in revenge porn against other pornographic content. Deep Neural Networks (DNNs) has become the best technique in computer vision processing and has great success in detecting pornography. This project aims to analyse the effectiveness of current techniques and propose a possible model for classifying non-consensual content.
**Key Words: **non-consensual content, revenge porn, DNNs, Deep Neural Networks, facial recognition.
Introduction
-
Background/Description:
Non-consensual content is the unsolicited proliferation of images/videos of a subject(s) with the intended (or unintended) consequence of social harm to the subject in the content. Non-consensual content predominantly refers to revenge porn, but more broadly can include non-pornographic content such as memes displaying an individual. Current techniques for classifying pornographic content can be categorised into three different methods. 1) skin-based methods, which are limited by the requirement of nude-hue pixels which are not strictly limited to pornographic content; 2) feature extraction and pattern recognition methods, which include visual bag-of-words, scale invariant feature transformation (SIFT), and self-similarity; and 3) deep learning-based models, which may utilise a combination of these techniques simultaneously to classify content. -
Purpose and Justification
The aim of the project is to discuss the effectiveness of neural network applications for classifying revenge porn across different content formats (video and images). Further, the project will discuss the ethics of consent in relation to ownership of pornographic and non-pornographic content. -
Problem Domain
The process of manually classifying porn videos, in particular revenge porn videos, is a tedious task due to the vast amount pornographic and non-pornographic content, the rate at which content is uploaded, across multiple platforms, and the capabilities for users to quickly reupload content that has been taken down. The development of advanced AI techniques for classifying pornographic content has focussed predominantly on Child Sexual Abuse content and image classification (less so video formats). As an individual’s reliance on the internet grows and the need for stronger privacy around content ownership becomes more important, there is a great need for effective techniques for classifying non-consensual content. Non-consensual content can have broad negative ramifications for the subject and therefore the takedown of content should be done quickly to prevent any further harm. -
Research questions:
- How effective are current porn classification techniques for different formats ?
- What are the current flaws and errors observed in existing models for identifying pornographic content ?
- How effective are classification techniques at identifying labelled non-consensual pornography among pornographic and non-pornographic content ?
- What are the ethical considerations of using personal information (e.g. facial images or pornographic content) to classify revenge porn ?
Research Methodology
- Methodology
The methodical practice conducted in this project will be done from the perspective of understanding the logic and the basics of research, rather than emphasising sophisticated methods (Hammersley, 2017). This reflects how Agile methodologies were undertaken during my project management subject and allowed for flexibility and adaptability during the project. However, due to the short period of time required to complete this project, the opportunities for reflexiveness will be limited.
The process will be conducted as such:
- Literary review
- Annotated Bibliography**
** - Data collection
My research will be, as described by Hammersley (2017) “reflective and thoughtful” – i.e., it will be aimed at trying to address the research questions presented; it will identify questions throughout the process; but it will leave opportunities for my project to take a reflective turn and examine some of those questions identified.
The following sources will be used:
-
Primo Search (Library Catalogue)
-
ProQuest Database
-
SpringerLink
-
Wiley Online Library
-
Google Scholar
-
Assumptions
As learnt in ITC505 ITC Project Management Course, stating the assumptions of the project is important to understand how/why it was started. A retrospective reflection in reference to my assumptions will allow me and my peers to understand the decisions I have made and the circumstances that led to the direction I went in my research. Below are the assumptions that I have made about the project:- Content sourced will be referenced in alignment of APA7 guidelines.
- My proposed project will be specific and small enough to be completed within 13 weeks.
- There will be sufficient literature to support my research project and meet the required minimum of 12 journal articles.
- While I will avoid bias or unconscious bias in my research project, I acknowledge that as a white Anglo-Saxon from middle class Australia, my opinions, perspectives, and experiences may influence my research and may not accurately reflect all perspectives.
-
Ethics Statements
- Pornography, Revenge Porn and Non-Consensual Content
- The topic of non-consensual content, in particular revenge porn, felt important enough that it required its own separate statement. To research and utilise non-consensual content requires the consent from individuals to study what they have reported as non-consensual – if that’s even possible to obtain. This appears to be a similar ethical constraint that arises in the study of Child Sexual Abuses (CSA) (Gangwar, 2021) which often conducts research without actual access to CSA databases (unless granted from an authority body). With these considerations comes strict guidelines, ethical and legal, that must be adhered to if my research seeks access to pornographic and/or non-consensual content. Research containing pornography, may need to censored, de-identified, or rendered in such a way that it is safe-for-work, or its contents disclosed appropriately.
- Research and Professional Ethics Statement
This Ethics Statement was written in guidance with the template provided by Ken Eustace (2020, Slide 15).- This project is being conducted under the directive to provide positive social good. The project therefore conforms to social responsibilities and will remain open to ideas throughout its development. As the topic matter, in particular consent and pornography, are personal and vulnerable areas I will treat these with care and refrain from personal judgement.
- As stated, the topic matter, in particular consent and pornography, must be researched and viewed with fairness and respect towards the sources of information whether anecdotal or statistical. Where possible or needed, research will be conducted with consent and personal information de-identified for the privacy of individuals. This is critical if this project utilises datasets of pornographic content that may or may not contain consensual content. The nature of this research domain emphasises the value of privacy and will retain the privacy of individuals whose content I use.
- The methodical collection and annotation of articles, reporting results, and any firsthand collection of data (surveys, interviews, models) will be obtained honestly and their purpose and usage communicated with transparency. This data will be stored and protected following the same ethical statements as above.
- Where needed, I will properly citate sources and give reference to any content sourced that is not my own. I will respect intellectual property and seek permission to publish if content is covered under copyright.
- Lastly, this project will respect the Academic Best Practices that I have been taught and conduct myself under at Charles Sturt University (CSU). These practices include not undertaking in plagiarism, contract cheating, or collusion.Communication between peers and within the cohort will be undertaken with the intention learning from each other by sharing ideas and critically analysing submitted work. All work published and submitted under my name will be mine and mine alone unless properly cited.
- Pornography, Revenge Porn and Non-Consensual Content
Preliminary Literature Review - short synopsis of literature
Project Plan
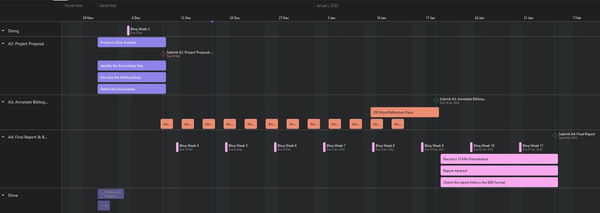
- Work breakdown structure (WBS)
The deliverables for this project – project proposal, annotated bibliography, blog, report, presentation – have been planned in Asana, using a GANTT structure and other visual formats like a WBS.
- Risk Analysis
I have used a Two-Variable Risk Matrix (Consequence/Likelihood) to calculate the risks that may occur in the project. The risks identified are not exhaustive and other risks that may develop during the project will be monitored and responded with the appropriate action.
**Risk | ****Consequence | ****Likelihood | ****Rating | **Action
--- | --- | --- | --- | ---
Personal circumstances and health issues delay the submission of deliverables |** 5 | 4 | 16 (Very High) |**** Deliverables will be developed and completed before the submission dates and if a delay occurs Kenneth Eustace will be notified.**
The project is too large a scope to be delivered within 13 weeks
4
3
12 (High)
The project scope will be monitored overtime in regards to the project plan. If the project can not be delivered within 13 weeks than the scope will be refined
Unable to find appropriate literature to support the project and address the assessment criteria
4
2
8 (Medium)
The scope of the research project can be refined.
Access to private and efficient internet is limited
3
1
3 (Low)
The project will be conducted at public locations where internet is available (e.g. libraries)
Content sourced or assessed in relation to this project is sensitive, inappropriate to publish or illegal to store
5
3
15 (High)
All content will be screened and verified for authenticity, to meet legal constraints, granted approval where needed, and censored to be “appropriate”.
Project deliverables become corrupt, destroyed, or altered in such a way that they can’t be submitted
5
2
10 (Medium)
The deliverables will be backed up on the cloud and stored locally. Versions/drafts published as blog posts will also serve as backups.
References
Eustace, K. (2021). ITC571 Topic 2 [Lecture Slides]. Emerging Technologies & Innovation. Interact 2. https://interact2.csu.edu.au/bbcswebdav/pid-4767120-dt-content-rid-17950645_1/xid-17950645_1
Gangwar, A., González-Castro, V., Alegre, E., & Fidalgo, E. (2021). AttM-CNN: Attention and metric learning based CNN for pornography, age and Child Sexual Abuse (CSA) Detection in images. Neurocomputing, 445, 81–104. https://doi.org/10.1016/j.neucom.2021.02.056
Hammersley, M. (2017). Methodology: Who needs it? [Video]. SAGE Publications. https://methods-sagepub-com.ezproxy.csu.edu.au/project-planner/philosophy-of-research
| Risk | Consequence | Likelihood | Rating | Action | |||||
| Personal circumstances and health issues delay the submission of deliverables | 5 | 4 | 16 (Very High) | Deliverables will be developed and completed before the submission dates and if a delay occurs Kenneth Eustace will be notified. | |||||